Getting Microsoft Graph API Delegated and Application permission IDs are definitely hard to find, if you are doing things right – the programmatic way.
Take this for example. We need to get the Microsoft Graph API Delegated and Application Directory.Read.All permission ID in Terraform. Therefore, you need to end up with something like this:
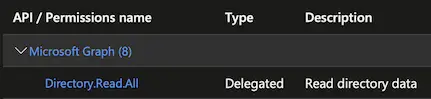
Prerequisites
- Azure subscription
- Azure AD Application
Delegated permissions
Delegated permissions are used when your Azure AD registered app requires an Azure API access as a signed-in user (signed-in user coming from your app).
Step 1. To get the id, run the following command:
az ad sp list --query "[?appDisplayName=='Microsoft Graph'].{permissions:oauth2Permissions}[0].permissions[?value=='Group.Read.All'].{id: id, value: value, adminConsentDisplayName: adminConsentDisplayName, adminConsentDescription: adminConsentDescription}[0]" --all
Output:
{
"adminConsentDescription": null,
"adminConsentDisplayName": null,
"id": "8114d053-7058-4d94-a7ea-e2dee97ba600",
"value": "Directory.Read.All"
}
Step 2. Copy the id and paste it in Terraform. For instance:
required_resource_access {
resource_access {
id = "8114d053-7058-4d94-a7ea-e2dee97ba600" # Directory.Read.All
type = "Scope"
}
}
Note(s):
- The id are randomly generated. Not trying to leak anything lol.
- Take notice of the permission type as part of the command in Step 1:
{permissions:oauth2Permissions}.
Application permissions
Application permissions are used when your Azure AD registered app is running as a background service without any signed-in user.
Step 1. To get the id, run the following command:
az ad sp list --query "[?appDisplayName=='Microsoft Graph'].{permissions:appRoles}[0].permissions[?value=='Directory.Read.All'].{id: id, value: value, adminConsentDisplayName: adminConsentDisplayName, adminConsentDescription: adminConsentDescription}[0]" --all
Output:
{
"adminConsentDescription": null,
"adminConsentDisplayName": null,
"id": "cd2ffcbd-39fd-47f9-a88f-683eb2be40e7",
"value": "Directory.Read.All"
}
Step 2. Copy the id and paste it in Terraform. For instance:
required_resource_access {
resource_access {
id = "cd2ffcbd-39fd-47f9-a88f-683eb2be40e7" # Directory.Read.All
type = "Role"
}
}
Note(s):
- Randomly generated id.
- Take notice of the permission type as part of the command in Step 1:
{permissions:appRoles}.
Conclusion
To recap:
- Delegated permissions → oauth2Permissions →
type = "Scope" - Application permissions → appRoles →
type = "Role"
Related post: Grant Azure AD Admin Consent programmatically (with Terraform).
Tried everything and nothing works? Let me know in the comment section below. On a side note, follow our official channel on Telegram.